Mimir Blog
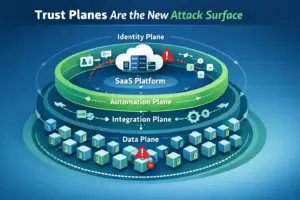
“Trust Planes” Are the New Attack Surface
Attackers are no longer “breaking in.” They are logging in—through stolen sessions, abused automations, and over-scoped integrations that your systems were designed to trust. Trust planes are the new attack surface. This post maps the planes, the kill chain, and the controls that matter—then shows why data-plane containment is the only durable way to prevent wholesale compromise.
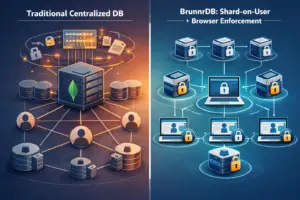
Preventing Cross‑Tenant Breaches: How BrunnrDB’s Architecture Contains Attacks Post‑MongoBleed
Introduction: Recent events have cast a spotlight on the risks inherent in traditional multi-tenant database architectures. Modern SaaS platforms often house all customer data in a single, massive multi-tenant data store. This creates an “all or nothing” scenario in security: if that central store is breached, the damage is rarely confined to a single account – it’s usually a wholesale compromise of large segments of the user basemimirsec.com. The recent “MongoBleed” vulnerability (CVE-2025-14847) underscored

Vendor Breach Containment: Making Integrations Safe Even When They Get Popped
Vendor breaches are no longer an edge case—they are a primary way attackers bypass your “front door” controls. A single compromised integration can turn into wholesale data access if it relies on long-lived tokens, broad permissions, unmanaged exports, or direct database connectivity. This post turns the “side doors” risk into an actionable containment checklist: minimize what vendors can reach, shorten how long access works, and reduce the value

When Healthcare Breaches Happen, Cyber Attacks Pay the Highest Price: Insights from Two Years of HHS OCR Data
Over the last two years, large healthcare data breaches reported to the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) have revealed a consistent pattern: almost all of the risk and almost all of the cost sit in one place – server aggregated data.

Sharding to Contain the Blast Radius of Data Breaches
Modern SaaS platforms sit on top of massive, multi-tenant data stores. When those stores are breached, the damage is rarely limited to a single record; it is often “wholesale” compromise of large slices of the user base. For a CISO or CTO, this is the critical risk: not that a record can be stolen, but that everything a given system knows becomes available in one incident.
When SaaS Fails, It Fails at Scale: Why Data-in-Use Protection Matters
Cloud and SaaS have become the default place to store and process sensitive data. They have also become the default place to lose it. Recent years have seen the same pattern repeat: a single weakness in a cloud platform, data-warehouse service, or widely used SaaS component is exploited once, and data for many organisations and millions of users moves at once. File-transfer vulnerabilities, data-warehouse credential campaigns, and third-party