Vendor Breach Containment: Making Integrations Safe Even When They Get Popped
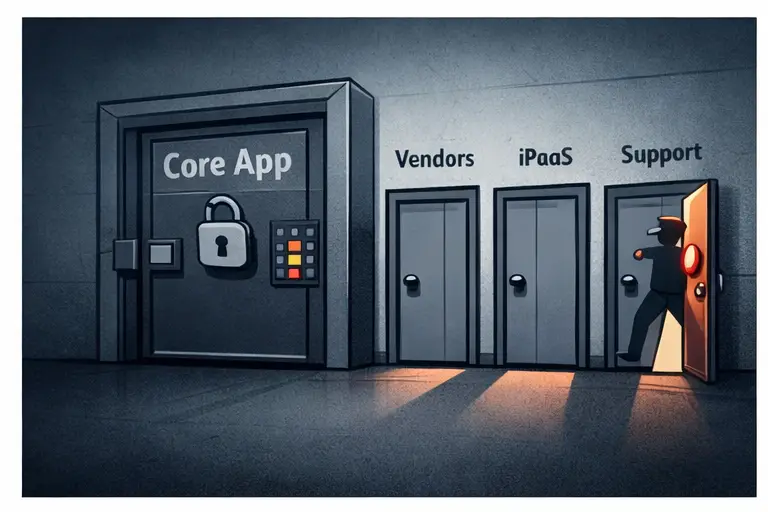
Vendor breaches are no longer an edge case—they are a primary way attackers bypass your “front door” controls. A single compromised integration can turn into wholesale data access if it relies on long-lived tokens, broad permissions, unmanaged exports, or direct database connectivity. This post turns the “side doors” risk into an actionable containment checklist: minimize what vendors can reach, shorten how long access works, and reduce the value of anything that leaks. You will find practical patterns—an integration gateway, curated exports, kill switches, and tight token scopes—that make stolen vendor access boring and keep blast radius small.